What is an ssh private key
command line

Effectively, any one possessing the key can decrypt the message being transferred. This is used as a secret private key for the interaction. The header tells us the encryption algorithm that was used: in. With , public key authentication improves security considerably as it frees the users from remembering complicated passwords or worse yet, writing them down. In a nutshell: A pair of encryption keys are generated which are mathematically linked to each other: a private key and a public key. . The motivation for using public key authentication over simple passwords is security.
Log in to a Linux server with an SSH private key on a Windows client
Browse other questions tagged or. Putting it all together After I had proved to myself it was possible to extract a private key from the registry, I put it all together in two scripts. To allow authorizing the host to the user, the user should be , before connecting. This includes the password typed into the console by the user, so credentials are always protected from network packet sniffers. You must save this private key to a text file. Host refers to the remote server you are trying to access, while the client is the computer you are using to access the host.
Improving the security of your SSH private key files — Martin Kleppmann’s blog
And for that case I can live with that. This works in a similar way to how the cipher is selected, as explained in the symmetric encryption section. Secure Shell provides strong and data communications between two computers connecting over an open network such as the internet. A user public key is a counterpart to user private key. Of those, 90% were no longer used.
Are SSH Keys or Passwords Better for SFTP Authentication?

The same key can be used to encrypt and decrypt messages read: section on symmetrical encryption. This is because many bots can simply brute force easy or default passwords and gain access to your account. I'm also not taking credit for the Python code - that should all go to soleblaze for his original implementation. When a large amount of data is being transmitted, session keys are used to encrypt this information. Is one really better or more secure than the other? Although passwords are encrypted, it is still not recommended to use passwords for secure connections.
What is Secure Shell (SSH)?
For example, you may want to access the root user, which is basically synonymous for system administrator with complete rights to modify anything on the system. The strength of the entire connection lies in the fact that the private key is never revealed, as it is the only component capable of decrypting messages that were encrypted using its own public key. One key pair is known as a host server key, the other as a user client key. When a private key is needed the user is asked to supply the passphrase so that the private key can be decrypted. These credentials securely pass through the symmetrically encrypted tunnel, so there is no chance of them being captured by a third party. I know that the name is not important. Entering a passphrase does have its benefits: the security of a key, no matter how encrypted, still depends on the fact that it is not visible to anyone else.
SSH Tutorial for Beginners

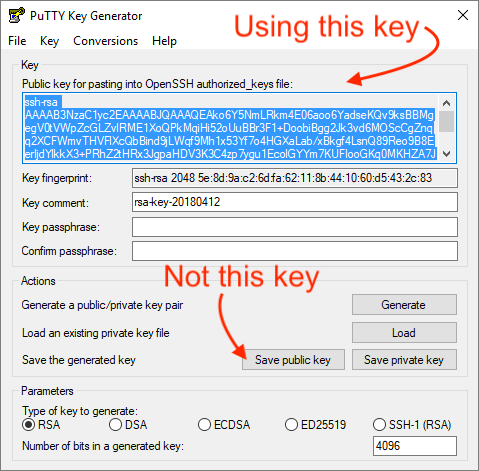
This process proves to the server that you have the corresponding private key to the public key it has on file. If you leave the passphrase blank, the key is not encrypted. If your password is correct, you will be greeted with a remote terminal window. The user is asked to enter the username, followed by the password. These numbers are used directly in the. They are only important to you, who has to manage them. Now you need to introduce your public key on Server 2.
openssh

host refers to the computer you want to access. Unlike the commonly known symmetric or secret-key encryption algorithms the public key encryption algorithms work with two separate keys. If you followed the instructions above, you may no longer be able to log into your servers. It organizes the secure connection by authenticating the client and opening the correct shell environment if the verification is successful. The sections below explain these briefly. You can increase security even more by protecting the private key with a passphrase.
Understanding SSH Key Pairs :: WinSCP

If your private key is not passphrase-protected, Pageant will add your private key without prompting you for a passphrase. I knew I had some sort of binary representation of a key, but I could not figure out the format or how to use it. Enter passphrase empty for no passphrase : It's up to you whether you want to use a passphrase. The private key must remain private i. This prime number value is also known as the seed value.
Left 4 dead download windows 7
Convert to pdf download online
Hitman 2016 pc game download compressed
